Viewing posts by admin
VPN services leak info via IPv6
Posted by: admin 10 years, 7 months ago
Earlier this year, we released a set of packer scripts that allow you to easily build a two-factor ready openvpn virtual appliance. We have updated the scripts to turn off IPv6 because it seems that VPN services using Openvpn can leak information via IPv6. (This was surely the easy fix. There may be better ones.)
Bridging Gunnar Gaps to create virtual circles
Posted by: admin 10 years, 7 months ago
If you haven't read Gunnar Peterson's post Security, Fast and Slow, please do so now. It is about how Security's natural tendencies grate the natural tendencies of Development. Security needs to adapt to make it easier for Development to make the right decisions to bridges such gaps. I now call these "Gunnar Gaps".
The two things that actually work in information security and how to deploy them.
Posted by: admin 10 years, 8 months ago
I was struck by this tweet by @chrisrollf: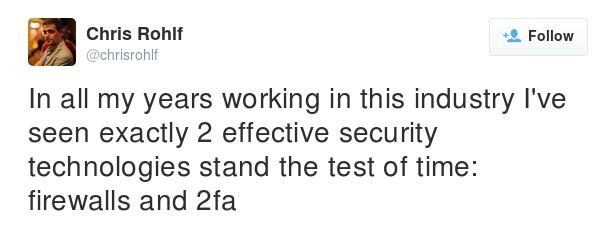
Sophos & Two-factor authentication
Posted by: admin 10 years, 8 months ago
We tested integrating WiKID for two-factor authentication to a Sophos UTM VPN. We documented the SSL-VPN, the LT2P /IPSec VPN and locking down administrator access. Before you do any of these, you must first enable two-factor authentication on the Sophos VPN.
Self-hosted or Authentication-as-a-service?
Posted by: admin 10 years, 9 months ago
So, we just released a freemium offering. That's typically a SaaS marketing move. Various hosted solutions have freemium two-factor authentication offerings. However, many, many people are uncomfortable outsourcing the keys to their kingdom. The reason we are willing to offer a piece of server software as a freemium product is that we are highly confident that the support costs will be minimal. Our server is very robust and rugged. It runs and runs. Come to our IRC channel (#wikid on freenode) and ask some customers. In fact, one of our biggest issues is that customers don't upgrade the server because they never have issues with it.
Authentication-as-a-Service offerings are not really 'software-free' either. RADIUS, the primary authentication protocol for all enterprises is not encrypted. So any AaaS service you use requires that you install software to proxy these requests. Our goal is to make it as easy to install WiKID as it is to install these proxies. On top of that, we offer advanced RADIUS functionality like Return-attributes, groups as well as other protocols like TACACS+.
In addition, WiKID is easier for the end-user than 'two-step authentication'. With WiKID, you get the OTP and login. That's better than logging in with a username and password, then getting an OTP and logging in. Users do not need an extra hassle.
Recent Posts
- Blast-RADIUS attack
- The latest WiKID version includes an SBOM
- WiKID 6 is released!
- Log4j CVE-2021-44228
- Questions about 2FA for AD admins
Archive
2024
2022
- December (1)
2021
2019
2018
2017
2016
2015
2014
- December (2)
- November (3)
- October (3)
- September (5)
- August (4)
- July (5)
- June (5)
- May (2)
- April (2)
- March (2)
- February (3)
- January (1)
2013
2012
- December (1)
- November (1)
- October (5)
- September (1)
- August (1)
- June (2)
- May (2)
- April (1)
- March (2)
- February (3)
- January (1)
2011
2010
- December (2)
- November (3)
- October (3)
- September (4)
- August (1)
- July (1)
- June (3)
- May (3)
- April (1)
- March (1)
- February (6)
- January (3)
2009
- December (4)
- November (1)
- October (3)
- September (3)
- August (2)
- July (5)
- June (6)
- May (8)
- April (7)
- March (6)
- February (4)
- January (427)
2008
- December (1)
Categories
- PCI-DSS (2)
- Two-factor authentication (3)
Tags
- wireless-cellular-mobile-devices (7)
- Two-factor authentication (10)
- Wireless, cellular, mobile devices (6)
- NPS (1)
- Phishing and Fraud (111)
- Active Directory (1)
- pam-radius (3)
- privileged access (2)
- Cloud Security (10)
- Mutual Authentication (60)
- Web Application Authentication (1)
- Authentication Attacks (99)
- pci (50)
- Security and Economics (97)
- WiKID (133)
- pam (2)
- VPN (1)
- Installation (2)
- RADIUS Server (1)
- Open Source (64)
- Tutorial (2)
- Strong Authentication (35)
- Information Security (137)
- Transaction Authentication (13)
- Miscellaneous (100)
- Linux (2)
- transaction-authentication (6)
- Two Factor Authentication (254)
