WiKID uses a hash of the server certificate stored on the authentication server to perform site/mutual authentication. When the user requests a one-time passcode (OTP), the hash is also sent from the server to the software token client. Before presenting the user with the OTP, the token client fetches the certificate from the website over the user's internet connection, hashes it and compares it to the hash retrieved from the server. If the hashes match, the URL is presented as validated and the default browser is launched to that URL. As usual, the OTP is automatically copied into the clipboard. This functionality is currently only available in the PC tokens.
First, I assume you have setup your Cisco ASA for two-factor authentication for sessions as previously described. You will not need to make any changes on the ASA for the configuration. It is all on the WIKID server.
Head to the WiKIDAdmin, Domains tab. Click the Edit link on the far right side if you have a domain or click Create A New Domain if you haven't. You will see the screen below:
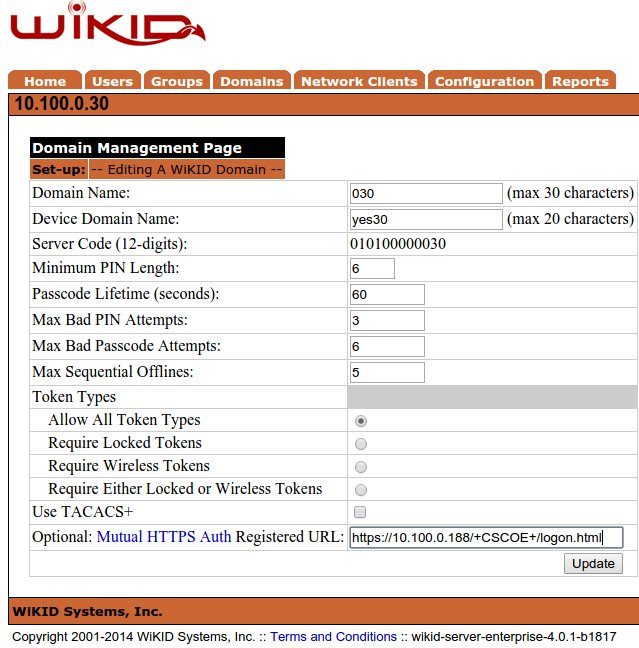
The only change I made was to add the SSL URL for the Cisco ASA to the optional Mutual HTTPS Auth URL box. Note that this is in our lab, so we are using 10.100.0.0 as the external network and 192.168.1.1. In most cases, your domain ID/server code would be based on an external IP and the Mutual HTTPS Auth URL would be the external network of the ASA.
Now, start (or restart) your WiKID token on your PC. Get a passcode and you will see that the browser is launched to the URL you enter. Great, it worked! But, it's a bit hard to see the value. Let's edit our iptables and make it fail. Here's what I entered on my test box:
sudo iptables -t nat -A OUTPUT -d 10.100.0.188 -j DNAT --to-destination 10.100.0.30
Now, when you try to get an OTP you get an error:
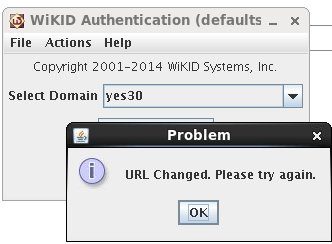
It's a bit cryptic, but enough to let your users know something bad has happened.
