This tutorial builds on this previous tutorial on how to configure the ASA 5500 for two-factor authentication for users. See that document for information on setting up a RADIUS Server Group which we use here.
Start the ASDM and navigate to Configuration, Device Management, Users/AAA, AAA Access. The first tab is Authentication. Click on Require authentication to allow use of privileged mode commands or select the types of connections below. Select the RADIUS Server Group you created previously. Check "Use local when server group fails" if you are so inclined.
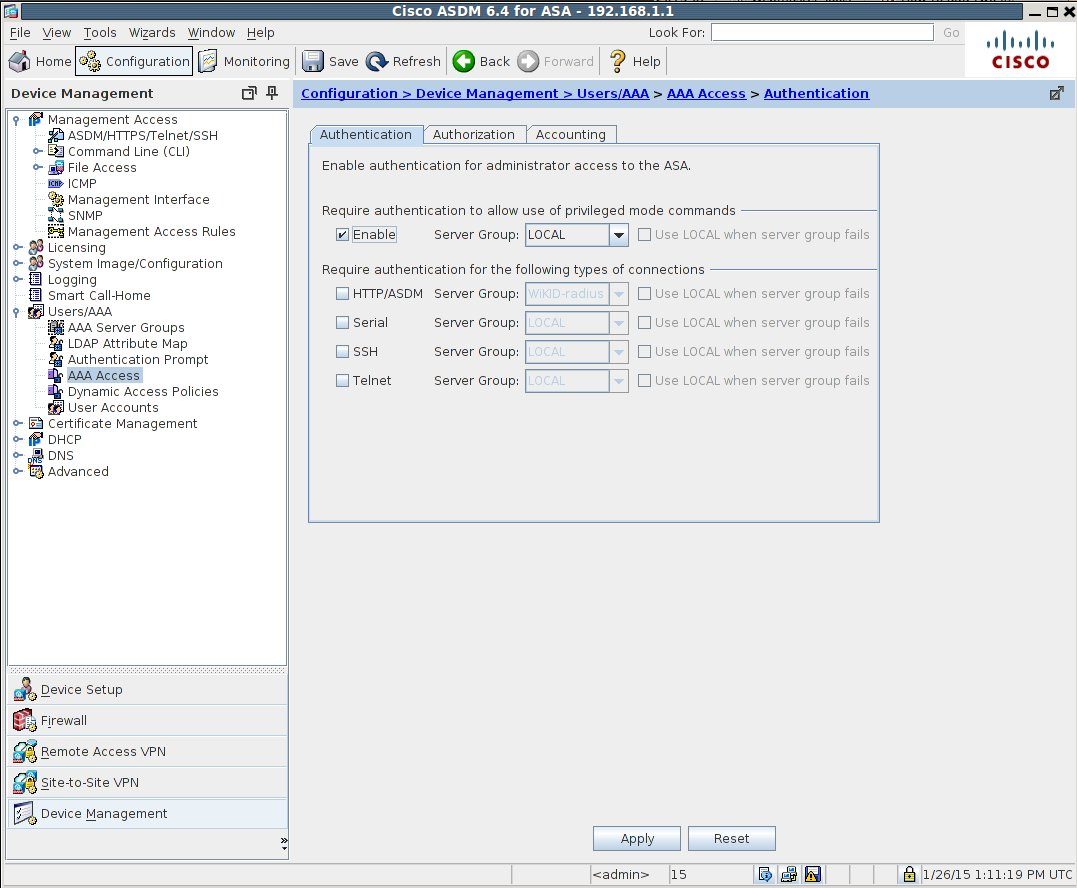
If you prefer to use the command line, you can use this command:
aaa authentication http console WiKID-radius LOCAL
Where WiKID-radius is the RADIUS Server Group and Local is configured as the backup.
