With the Sophos UTM, you first configure the device to support two-factor authentication via an Authentication Service, then assign/require that service for various services. To require two-factor auth for administrators, you associate the WebAdmin service with a group of users required to use that service.
Click on Management/WebAdmin Settings. click on the folder icon on Allowed Administrators. The Users/Groups list will come up. Grab the Radius Users group you set up earlier and drop it into the Allowed Administrators Group. I do not recommend removing the existing admin user. (It's not good to be locked out of your firewall.)
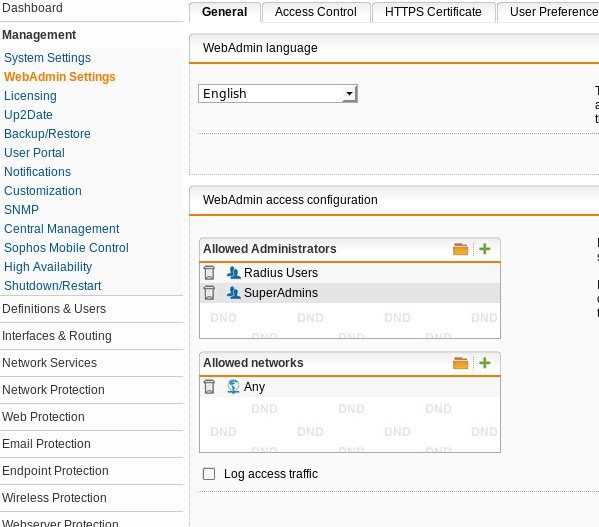
Click Apply. Log out and you should be able to log back in with a valid WiKID users. Now, how to keep your VPN users from logging in as a WebAdmin? The tricky part is on the WiKID server because RADIUS uses the IP address of the client to process the authentications. If you are using a RADIUS server for your VPN users, you can a direct network client using the IP address of your Sophos and associate that with a WiKID domain consisting of your Admins.
