Posted by:
admin
10 years, 8 months ago
I was struck by this tweet by @chrisrollf: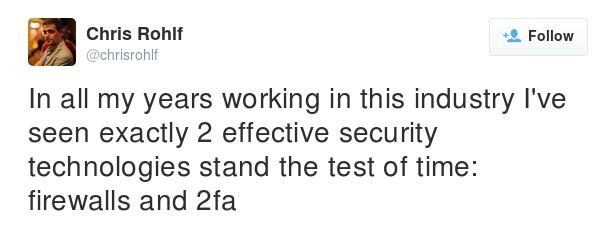
Because of the truth of it (and yeah, because we sell two-factor authentication). IPS/IDS, anti-virus, etc really haven't performed as advertised. You can see the move to de-perimeterization pushing all those security products, when just implementing two-factor authentication would have been as or more effective.
Thanks to this year's Verizon DBIR, we can see the impact of these two technologies and how to implement them. Verizon has aggregated their mitigation recommendations and summed the percentage of time where a Critical Security Control should have been applied.
We gathered up all the nuggets of mitigation wisdom from our reviews and tallied up the
percentage of incidents where a CSC control could be applied as the recommended strategy.
(That's a direct quote, btw, the DBIR is saying 'Critical Security Control control'.)
I have amended the table to include a column on if the control can be supplied by one of the two 'effective security technologies'.
| CSC | Description | % | Category | Notes |
|---|---|---|---|---|
| 13-7 | Two-factor authentication | 24% | Visibility/Attribution | 2FA: The biggest bang for your security buck. |
| 6-1 | Patching web services | 24% | Quick Win | |
| 11-5 | Verify need for Internet-facing devices |
7% | Visibility/Attribution | Firewall: You should do this on setup and periodically. Remember - it's easy to block ports and see what breaks. |
| 13-6 | Proxy outbound traffic | 7% | Visibility/Attribution | Firewall: We've suggested combining this with 2FA too. |
| 6-4 | Web application testing | 7% | Visibility/Attribution | |
| 16-9 | User lockout after multiple failed attempts | 5% | Quick Win | 2FA (etc). All 2FA systems have this feature. |
| 17-13 | Block known file transfer sites | 5% | Advanced | Firewall: Most firewalls offer URL blocking. |
| 5-5 | Mail attachment filtering | 5% | Quick Win | Firewall: Most firewalls offer attachment filtering. |
| 11-1 | Limiting ports and services | 2% | Quick Win | Firewall - Pretty much the point of VPNs. |
| 13-10 | Segregation of networks | 2% | Configuration/Hygiene | Firewall. Your firewall should be able to create virtual private networks. |
| 16-8 | Password complexity | 2% | Visibility/Attribution | OS - but if you use 2FA in more places, it's better. |
| 3-3 | Restrict ability to download software | 2% | Quick Win | Firewall |
| 5-1 | Anti-virus | 2% | Quick Win | |
| 6-8 | Vet security process of vendor | 2% | Configuration/Hygiene | Require 2FA for vendor access for control. |
I've always been a "work with what you have" and "get the most out of what you have" type of person. This list screams that. I also think that companies will need to consider the source. While the DBIR is a great resource, it is a work in progress and your industry may be under-represented or your company may be different. And security is a moving target. The description of "Vet security process of vendor" seems a bit vague. I suspect that many organizations are now considering deploying some form of "Privileged access management" solution to monitor not only internal account but also vendor accounts. If so, they should use two-factor auth for their PAM solution (and you should make sure your PAM solution supports RADIUS).
Share on Twitter Share on FacebookRecent Posts
- Blast-RADIUS attack
- The latest WiKID version includes an SBOM
- WiKID 6 is released!
- Log4j CVE-2021-44228
- Questions about 2FA for AD admins
Archive
2024
2022
- December (1)
2021
2019
2018
2017
2016
2015
2014
- December (2)
- November (3)
- October (3)
- September (5)
- August (4)
- July (5)
- June (5)
- May (2)
- April (2)
- March (2)
- February (3)
- January (1)
2013
2012
- December (1)
- November (1)
- October (5)
- September (1)
- August (1)
- June (2)
- May (2)
- April (1)
- March (2)
- February (3)
- January (1)
2011
2010
- December (2)
- November (3)
- October (3)
- September (4)
- August (1)
- July (1)
- June (3)
- May (3)
- April (1)
- March (1)
- February (6)
- January (3)
2009
- December (4)
- November (1)
- October (3)
- September (3)
- August (2)
- July (5)
- June (6)
- May (8)
- April (7)
- March (6)
- February (4)
- January (427)
2008
- December (1)
Categories
- PCI-DSS (2)
- Two-factor authentication (3)
Tags
- wireless-cellular-mobile-devices (7)
- Two-factor authentication (10)
- Wireless, cellular, mobile devices (6)
- NPS (1)
- Phishing and Fraud (111)
- Active Directory (1)
- pam-radius (3)
- privileged access (2)
- Cloud Security (10)
- Mutual Authentication (60)
- Web Application Authentication (1)
- Authentication Attacks (99)
- pci (50)
- Security and Economics (97)
- WiKID (133)
- pam (2)
- VPN (1)
- Installation (2)
- RADIUS Server (1)
- Open Source (64)
- Tutorial (2)
- Strong Authentication (35)
- Information Security (137)
- Transaction Authentication (13)
- Miscellaneous (100)
- Linux (2)
- transaction-authentication (6)
- Two Factor Authentication (254)
