We're starting to see a lot more interest in adding two-factor authentication to virtual desktop services. Virtual desktops make a lot of sense for a lot of reasons and they get around one big hassle: the lack of support for two-factor authentication in the Microsoft GINA via standard networking protocols such as radius.
On the other hand, adding two-factor authentication using Radius to VMWare Viewer is a breeze. Sadly, the resulting set up is less than optimal.
Start by logging into the View Administrator on the View 5.1 Connection Server using https://hostname/admin.
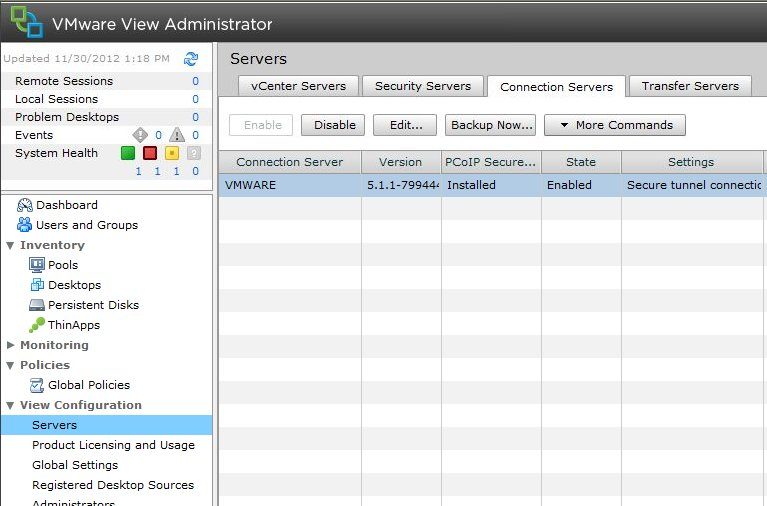
Click on Servers in the left panel and then the Connection Servers tab in the right window. Select the Connection Server and select Edit. Under Authentication > Advanced Authentication, set the two-factor authentication option to RADIUS and under Authenticator select Create New Authenticator.
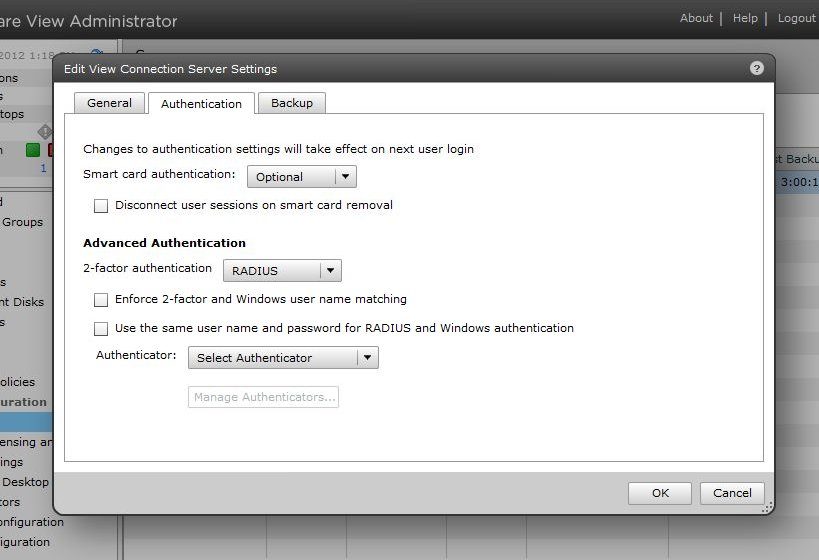
Enter a label such as 'WiKID Server' and a Description such as 'two-factor authentication server'. Enter the IP address or hostname of the WiKID server and a shared secret (be sure to enter this same secret in the Network Client on the WiKID server). You can use any of the authentication types. Leave the authentication port as 1812. Set the Accounting Port to 0 as the WiKID server doesn't support accounting.
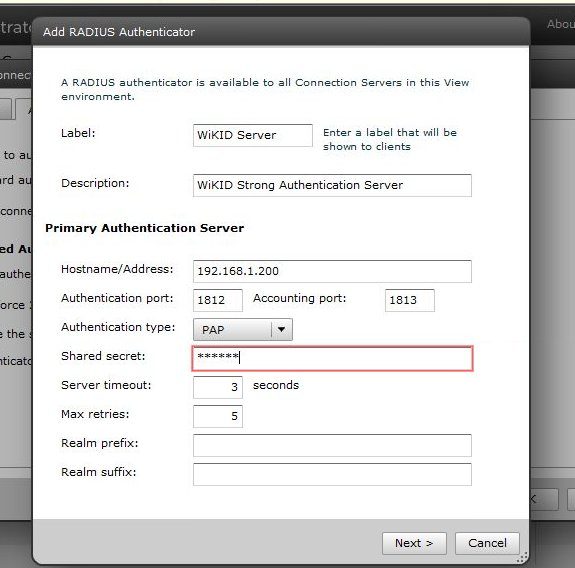
On the WiKID server, you will need to create a Network Client for the VMWare View server and restart WiKID. That's it. Pretty easy. Unfortunately, the way that VMWare has integrated windows authentication is less than user friendly.
First start up your VMWare View connection client and point it to your VMWare View server:
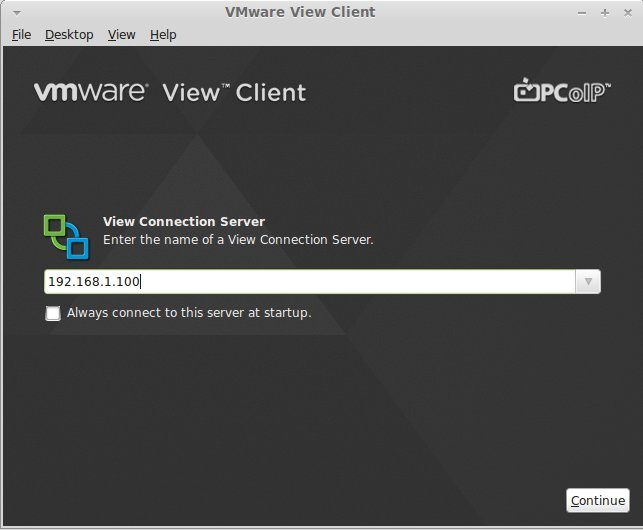
Then you login with your user name and one-time password:
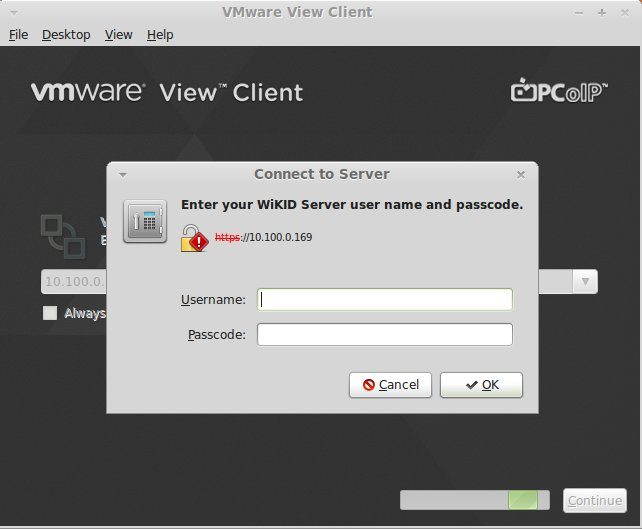
Next you need to login again with your AD credentials!
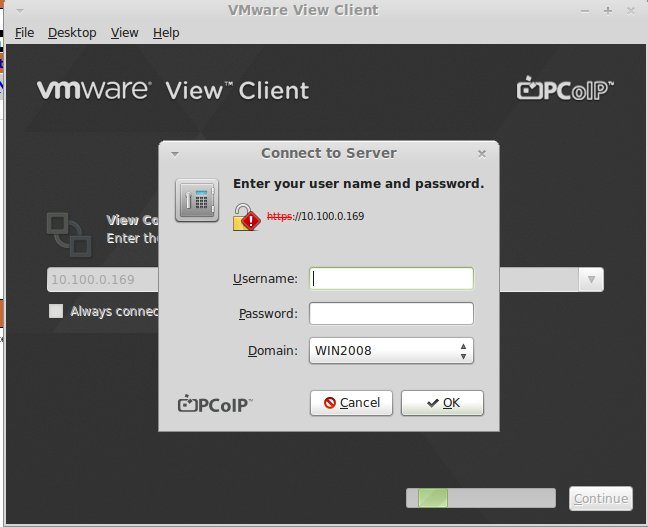
This is completely unnecessary as NPS, the Microsoft Radius plugin, will do authorization based on the users AD username and then proxy the username and OTP to the WiKID server for two-factor authentication. Why make security harder for the users?
UPDATE: VMWare has added an option so the user doesn't have to re-enter their username. Enable "Enforce same username option" and the username will be pre-populated from the first login. It would still be better if VMWare allowed only RADIUS as the auth source instead of requiring this 'two-step authentication'. WiKID combined with NPS is a better solution for including AD authorization.
